Encrypting with Double Transposition

Requires a Wolfram Notebook System
Interact on desktop, mobile and cloud with the free Wolfram Player or other Wolfram Language products.
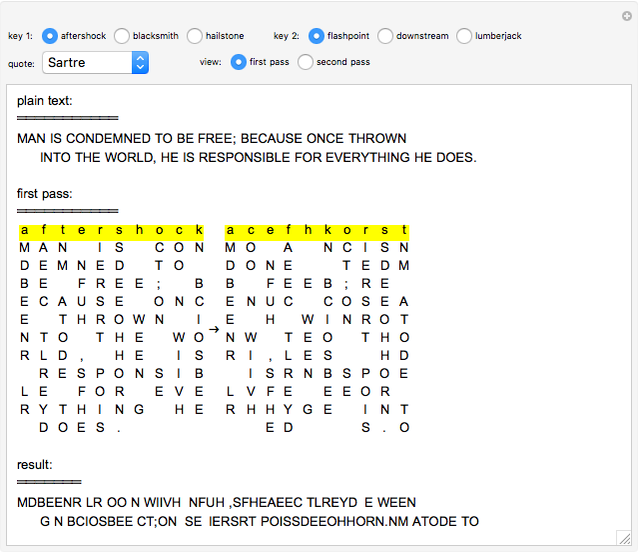
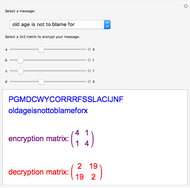
This Demonstration shows the mechanics of double transposition, a hand cipher used by both sides in the Second World War.
Contributed by: Raymond Yang (February 2019)
Open content licensed under CC BY-NC-SA
Details
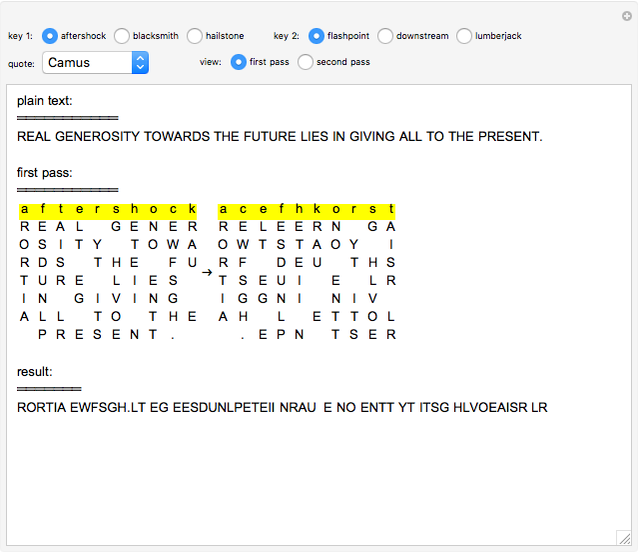
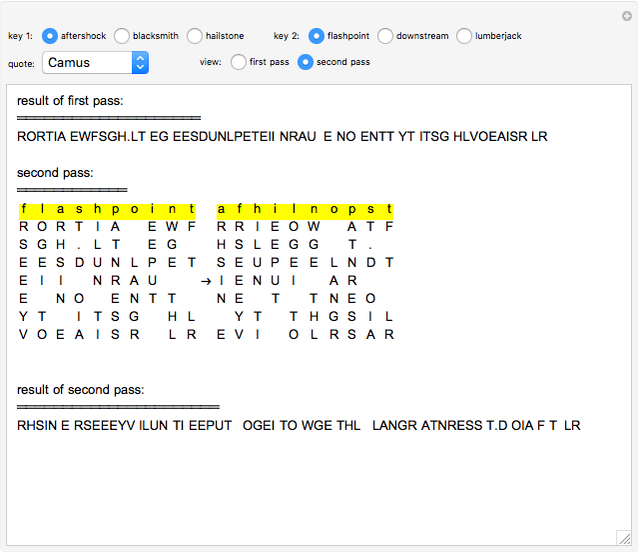
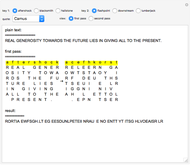
The double transposition encryption method works by arranging the message (set by the "quote" option) in a grid with the width determined by the encryption key ("key 1" and "key 2") and then reading off the columns in alphabetical order to create the output. This output is then passed through the transposition method a second time with a different key (hence double transposition) to create the final ciphertext. For decryption, the ciphertext is written into the columns based on the alphabetical order of the letters in the key, then reading off the resulting grid horizontally, and repeating for the "second pass".
This method works best with isograms for encryption keys, though non-isogram encryption keys can be used if a method of distinguishing identical letters is determined.
This was a project for Advanced Topics in Mathematics II, 2018–2019, Torrey Pines High School, San Diego, CA.
Snapshots
Permanent Citation